When I first dived into learning IPsec, I’ll be honest—it felt like I was staring into a whirlwind of confusing terms.
Tunnels, phases, protocols… everything seemed jumbled together, and nothing really clicked at first.
But here’s what I figured out: IPsec isn’t just one protocol—it’s a powerful framework made up of several moving parts. Each piece has a clear purpose, from how the tunnel is established, to how the keys are exchanged, to how the data is protected. It all works together like a puzzle.
In this blog, I’ve laid out a simple roadmap that breaks down the entire IPsec concept into manageable chunks. If you take time to understand each piece of this framework, I guarantee it’ll all make sense—and you’ll feel confident about it.
So, let’s walk through what you really need to know to master IPsec.
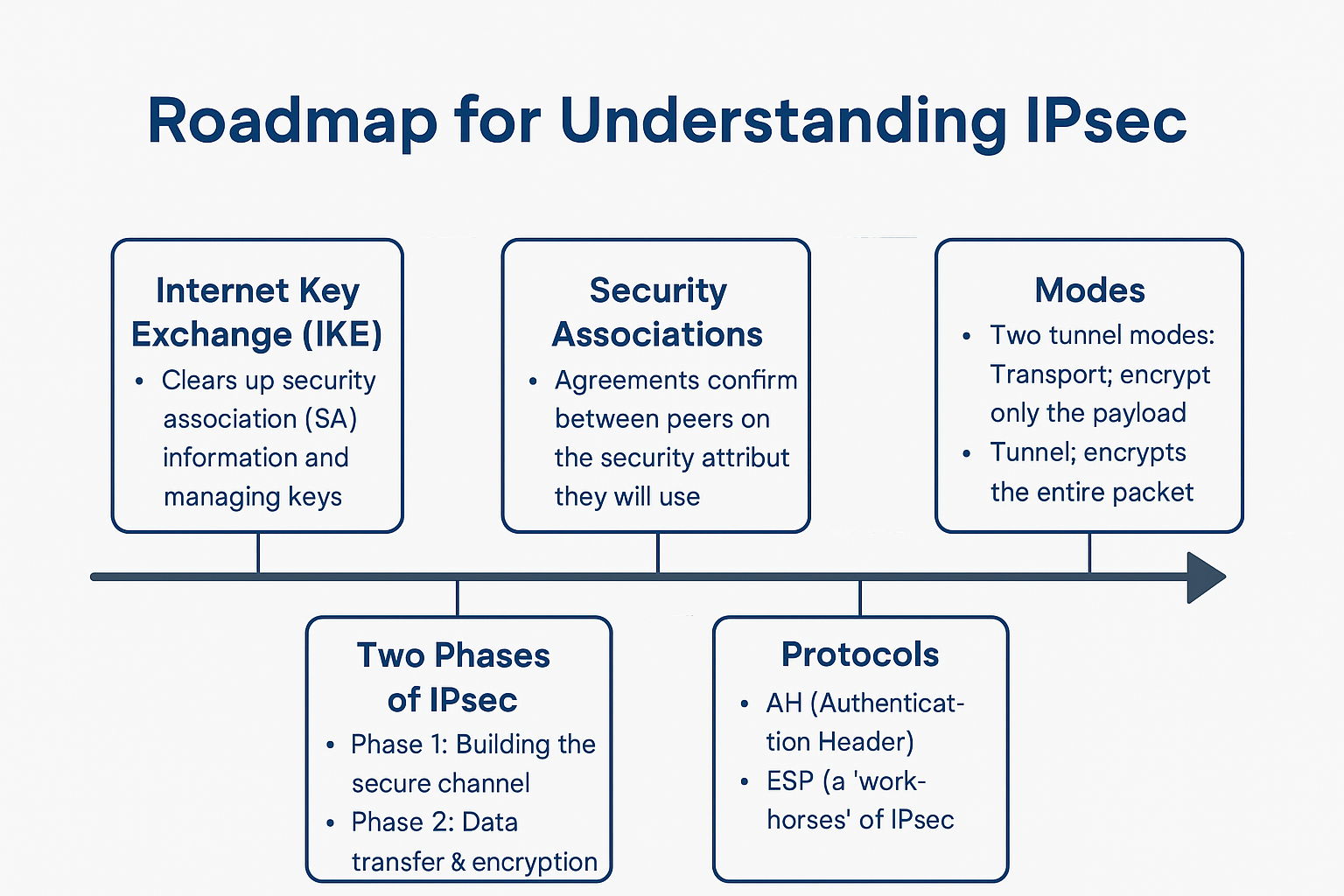
Here’s your IPsec learning blueprint
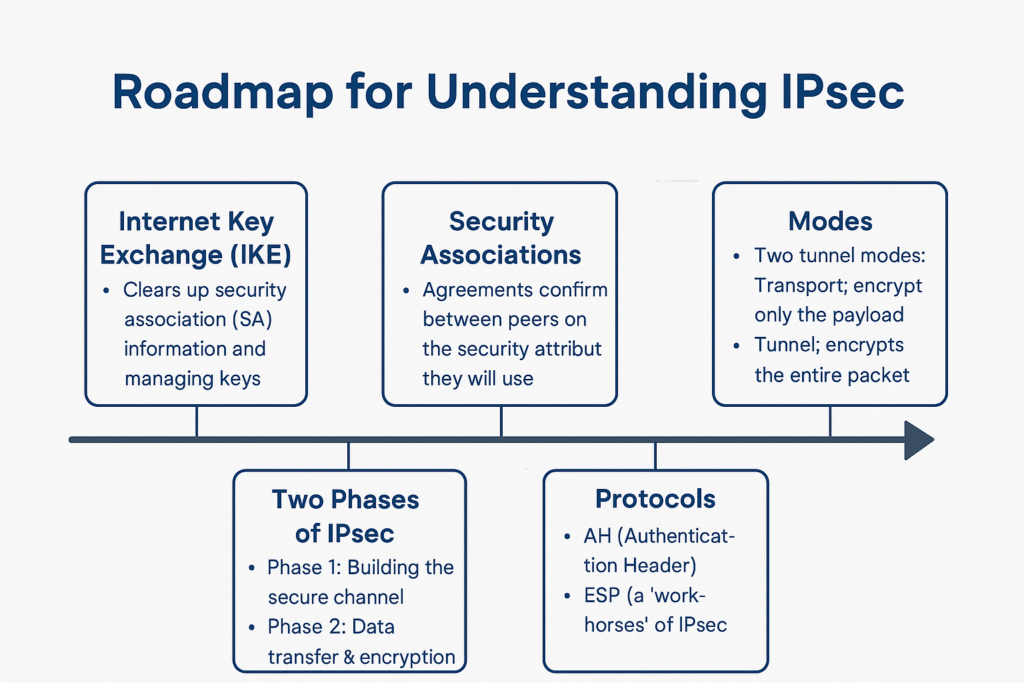
1. What is IPsec?
- Definition and Purpose
- Why IPsec is needed
- Use Cases (e.g., Site-to-Site VPN, Remote Access)
2. IKE (Internet Key Exchange)
- What is IKE?
- Role of IKE in IPsec
- Difference between IKEv1 vs IKEv2
3. Security Association (SA)
- What is a Security Association?
- Unidirectional nature of SAs
- SA in Phase 1 vs SA in Phase 2
4. Phases of IPsec
- Phase 1
- Purpose: Create secure channel
- Modes: Main Mode vs Aggressive Mode
- Authentication: Pre-shared Key, RSA
- Result: ISAKMP SA
- Phase 2
- Purpose: Negotiate IPsec tunnel
- Mode: Quick Mode
- Result: IPsec SA for actual data transfer
5. IPsec Modes
- Tunnel Mode – Encrypts full IP packet (used in site-to-site)
- Transport Mode – Encrypts only the payload (used in host-to-host)
- Comparison between Tunnel vs Transport
6. IPsec Protocols
- ESP (Encapsulating Security Payload) – Encrypts and authenticates
- AH (Authentication Header) – Only authenticates, no encryption
- Differences: ESP vs AH
7. Encryption & Hashing Algorithms
- Examples: AES, 3DES, DES (Encryption)
- SHA1, SHA256, MD5 (Integrity)
- How to choose algorithms
8. NAT Traversal (NAT-T)
- Why NAT breaks IPsec
- How NAT-T fixes it (UDP port 4500)
9. Lifetime & Rekeying
- SA lifetime defaults (e.g., 1 hour for Phase 2)
- When and why rekeying is done
10. Troubleshooting IPsec VPN
- Common issues
- Logs and debugging
- Verifying tunnels with CLI commands