Learn the difference between IPsec Tunnel Mode and Transport Mode in simple terms. Understand how each mode works, when to use them, and why they matter for secure network communication.
When it comes to securing data over the internet, IPsec (Internet Protocol Security) is one of the most trusted guardians in the networking world. It’s like having a secret tunnel where your data travels unseen — or sometimes, just locking up the important part of the message while letting the envelope stay visible.
This brings us to two modes of IPsec: Tunnel Mode and Transport Mode. They might sound similar, but trust me — the way they work is different, and understanding this difference is essential if you want to configure networks like a pro.
Let’s break it down in plain English, without diving into overly technical jargon.
First, what is IPsec doing here?
IPsec is all about securing communication between two points — whether those points are two computers, two networks, or even a remote worker’s laptop and a company’s internal servers.
It works on the network layer of the OSI model, meaning it can protect not just applications, but the entire flow of network traffic.
Think of IPsec as a security guard for your data:
- It can encrypt your data so that even if someone intercepts it, they can’t read it.
- It can authenticate the source, ensuring the data hasn’t been tampered with.
- It can protect against replay attacks by checking that old packets aren’t maliciously resent.
Now, the way this “guard” operates depends on whether you’re in Tunnel Mode or Transport Mode.
But Wait… If We Already Have IKE Phase 1 & Phase 2, Why Do We Still Need Tunnels?
Before diving into Tunnel Mode and Transport Mode, let me share the exact thought that popped into my mind when I first learned about IPsec:
“Hold on… We already have IKE SA Phase 1 and Phase 2 to handle encryption and authentication. Then why are we talking about Tunnel Mode and Transport Mode again?”
If you’ve wondered the same thing, you’re not alone — and here’s the clear answer.
Step 1 – What IKE SA Phases Really Do
The Internet Key Exchange (IKE) process isn’t actually encrypting your user data directly.
Instead, it’s a negotiation process between two endpoints to decide:
- How they will authenticate each other
- Which encryption algorithms they’ll use
- What keys they’ll use for protecting the traffic
It works in two phases:
- Phase 1 (IKE SA) – The two endpoints (say, your laptop and a VPN gateway) create a secure management channel.
This is used only for control messages — basically, the two parties agreeing:
“Let’s talk in private about how we’ll protect our real data.” - Phase 2 (IPsec SA) – Inside that private channel, they now decide the exact protection details for your real network traffic — algorithm choice, key length, lifetime, etc.
This creates the Security Associations that will be used to secure actual IP packets.
At the end of Phase 2, we have:
- A safe channel for management (Phase 1 result)
- Agreed encryption & authentication settings for real data (Phase 2 result)
But… your actual data hasn’t been encrypted yet.
Step 2 – Where Tunnel Mode and Transport Mode Step In
Think of IKE as the planning stage and Tunnel/Transport as the execution stage.
- IKE decides the encryption rules and generates the keys.
- Tunnel or Transport mode uses those rules and keys to wrap and protect your actual IP packets.
They’re not “extra” encryption — they’re the format in which IPsec applies encryption to your traffic:
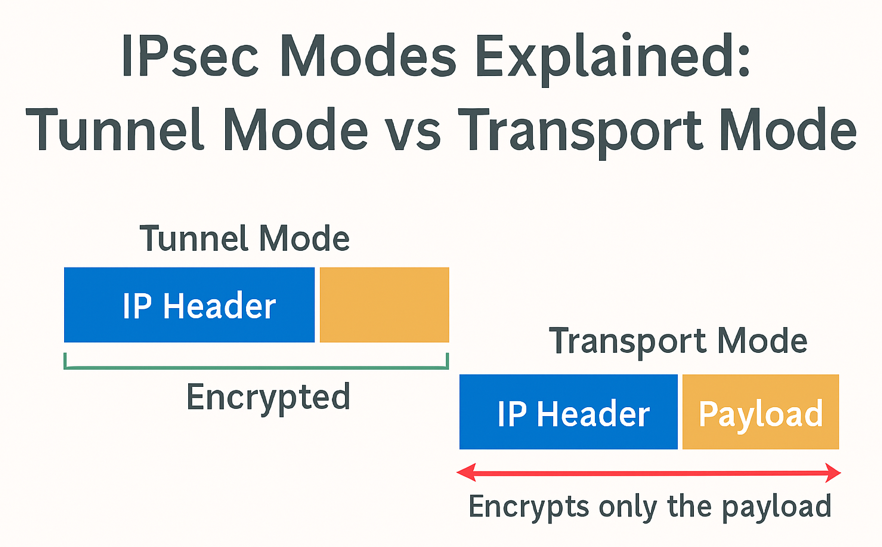
- Tunnel Mode → Encrypts the entire original IP packet and puts it inside a new packet.
- Transport Mode → Encrypts only the payload while leaving the original IP header visible.
Step 3 – Why the Tunnel Still Matters
If we stopped at IKE Phase 2, we’d have:
- Two devices that trust each other
- A set of keys and algorithms agreed upon
But without Tunnel or Transport mode:
- No packet formatting would occur
- Your application data would still travel in the clear, even though we have the keys to protect it
IKE is like signing a contract to use a secure lock system.
Tunnel or Transport mode is actually locking up the items before sending them.
A Simple Analogy
- IKE Phase 1 – You meet a friend in person and agree on a secret codebook for sending letters.
- IKE Phase 2 – You both agree which page of the codebook to use for this week’s letters.
- Tunnel/Transport Mode – You finally start writing letters and either:
- Seal the whole letter and envelope inside another envelope (Tunnel Mode)
- Seal only the content inside the existing envelope (Transport Mode)
Without step 3, the “secure communication” is just an idea — nothing is actually being protected.
In short:
IKE SA Phases 1 & 2 set the stage by negotiating and agreeing on the security rules.
Tunnel Mode and Transport Mode are how those rules are actually applied to your data packets.
Ah, now it makes sense why these modes are so important! Let’s dive deeper and explore what each mode actually does.
1. Tunnel Mode – The “Full Envelope” Protection
Imagine you write a letter (your data packet). You already have an envelope with the sender and receiver’s address (the original IP header). But before sending it, you decide to put that entire envelope into a bigger, more secure envelope with a different set of addresses.
That’s Tunnel Mode in action.
How Tunnel Mode Works:
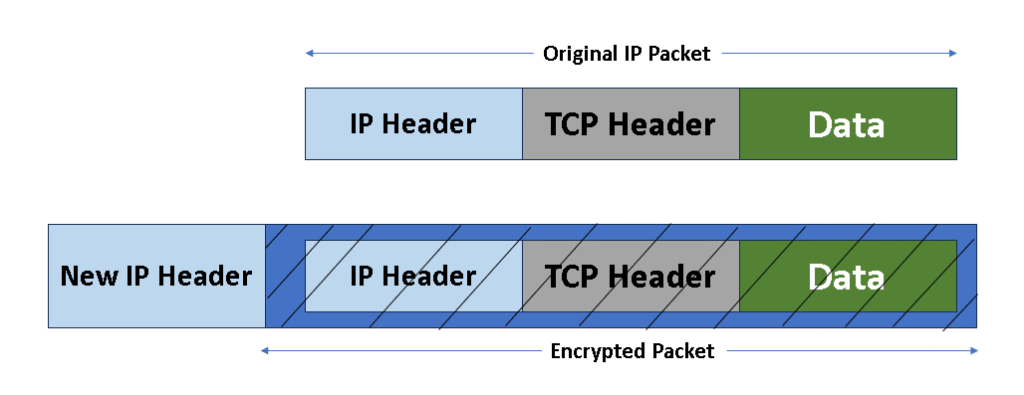
- It encrypts the entire original IP packet (including both the IP header and the data payload).
- Then, it wraps it in a new IP packet with a new IP header.
- This is like placing your original message (with its address) inside a new sealed package with a different address.
Where Tunnel Mode Is Used:
- Site-to-site VPNs: When two networks (like two company branches) need to communicate securely over the internet.
- Gateway-to-gateway communication: The devices at both ends are routers or VPN gateways, not individual user devices.
Why Tunnel Mode?
Because it hides everything — even the original sender and receiver’s IP addresses. Perfect for crossing untrusted networks like the internet without giving away details.
2. Transport Mode – The “Seal Only the Message” Approach
Now imagine you have your letter and envelope, but instead of putting it in another envelope, you just seal the contents inside the envelope so no one can read the message — but they can still see where it’s coming from and where it’s going.
That’s Transport Mode.
How Transport Mode Works:
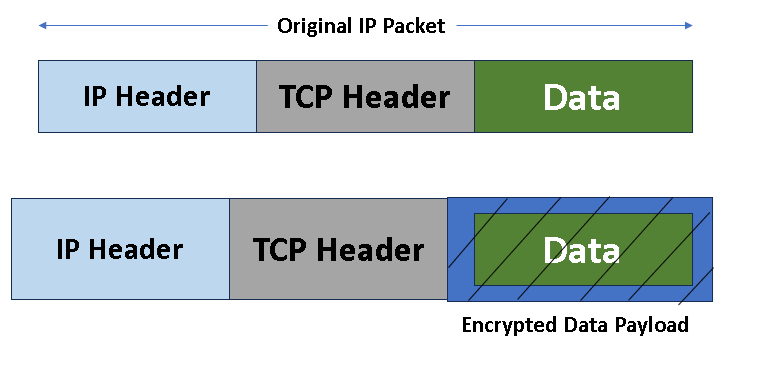
- It encrypts only the payload (the actual data) inside the IP packet.
- The original IP header remains untouched.
- This means that routers along the way can still read the source and destination addresses to deliver the packet.
Where Transport Mode Is Used:
- Host-to-host communication: When two devices communicate directly without going through a VPN gateway.
- Common in scenarios where the two endpoints trust each other but still want to keep the conversation private from outsiders.
Why Transport Mode?
It’s more lightweight because it doesn’t add a new IP header. That means less overhead and faster communication when full IP header protection isn’t necessary.
Tunnel Mode vs Transport Mode – Side-by-Side
Let’s compare them so you can easily decide which fits your situation:
| Feature | Tunnel Mode | Transport Mode |
| What’s Encrypted | Entire original IP packet (header + payload) | Only the payload (data) of the IP packet |
| IP Header Visibility | Original IP header is hidden (replaced with a new one) | Original IP header remains visible |
| Overhead | Higher (because of extra IP header) | Lower (no extra IP header) |
| Typical Use Case | Site-to-site VPNs, gateway-to-gateway communication | Host-to-host communication |
| Privacy Level | Full privacy – even hides sender and receiver info | Partial privacy – hides data, but not IP info |
How to Remember the Difference
- Tunnel Mode = Total concealment (everything is wrapped up and hidden).
- Transport Mode = Targeted concealment (just the message is hidden).
If you picture a tunnel, everything inside is invisible from the outside — that’s Tunnel Mode.
If you picture a sealed letter, the address is still on display — that’s Transport Mode.
Final Thoughts
Both Tunnel Mode and Transport Mode are valuable — it’s not about one being better than the other, but about choosing the right one for the job.
- If you need network-to-network privacy and want to hide all details of communication → Tunnel Mode is your friend.
- If you need direct device-to-device privacy without hiding IP headers → Transport Mode is the right choice.
By understanding these two modes, you’re already ahead of many people who configure VPNs without knowing what’s actually happening under the hood.
After all, securing data isn’t just about clicking “enable encryption” — it’s about knowing how it’s protected.