BGP Route Reflector
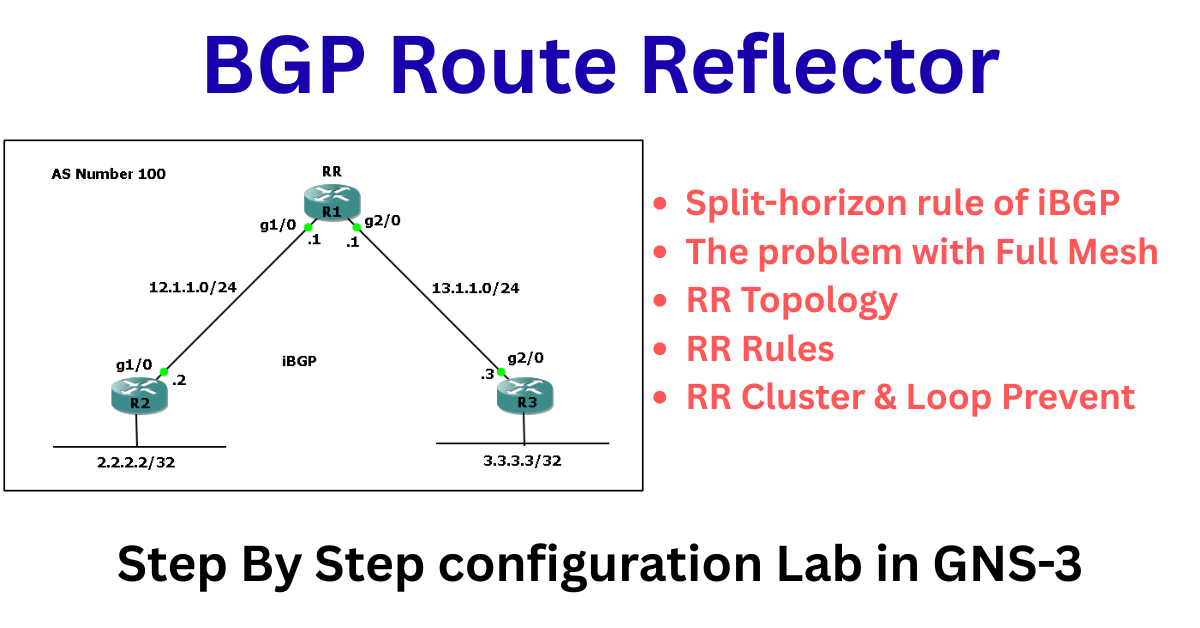
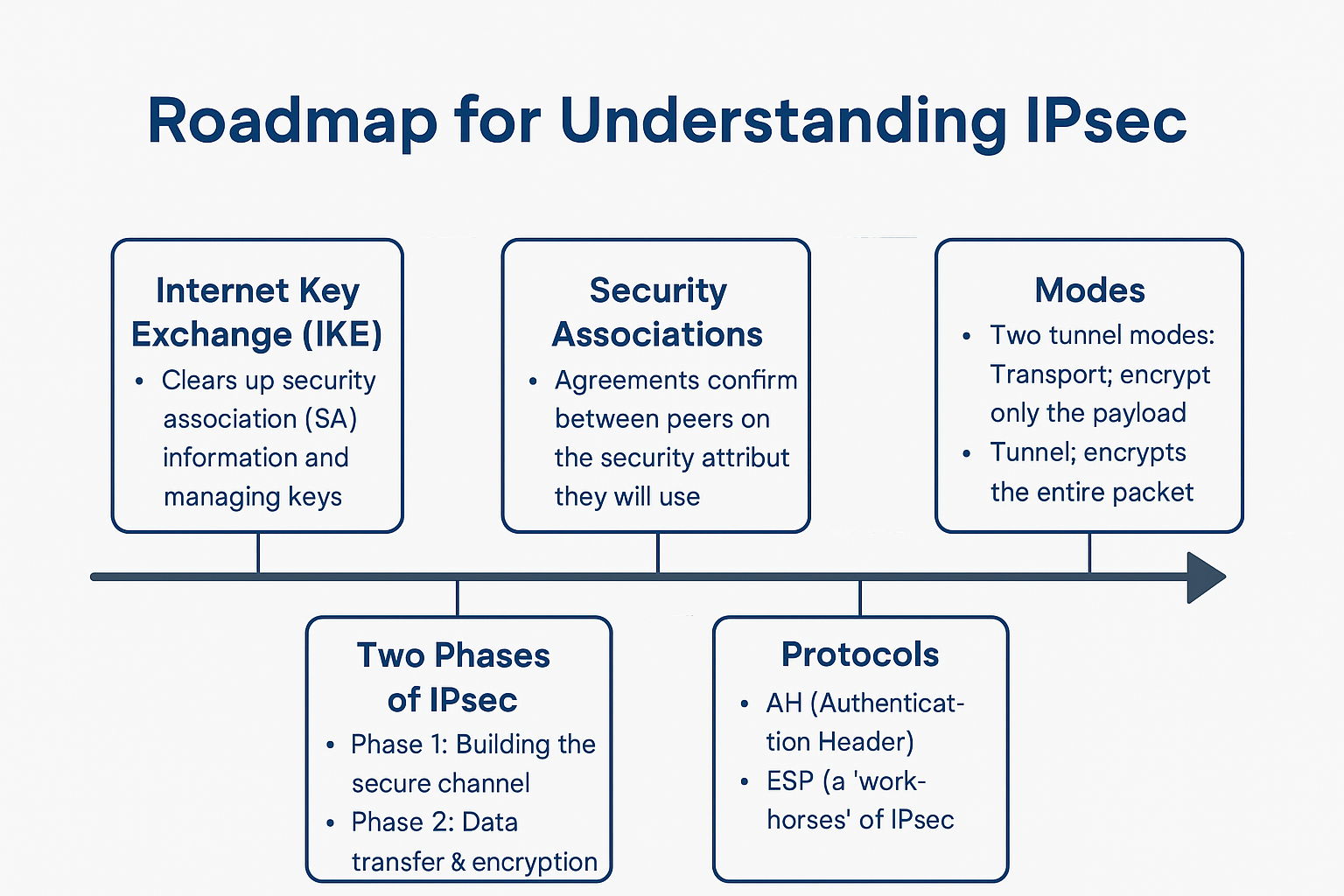
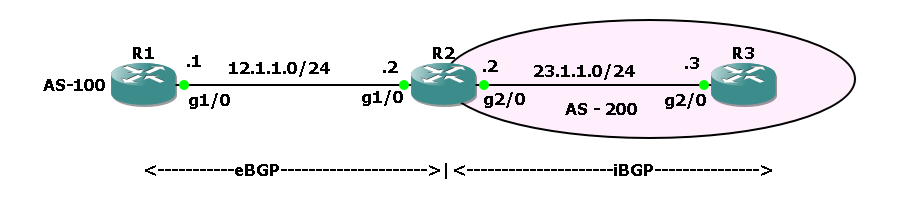
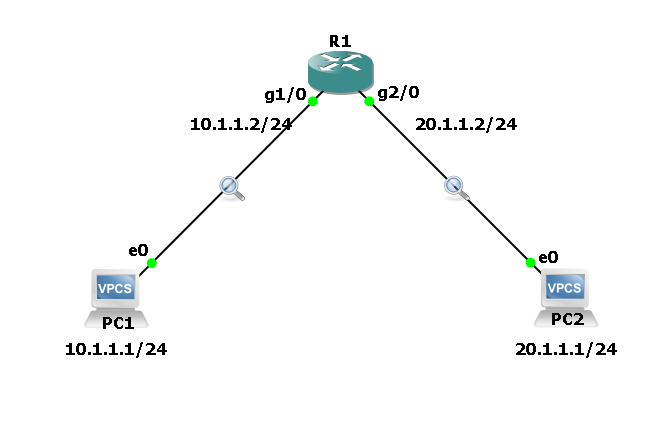
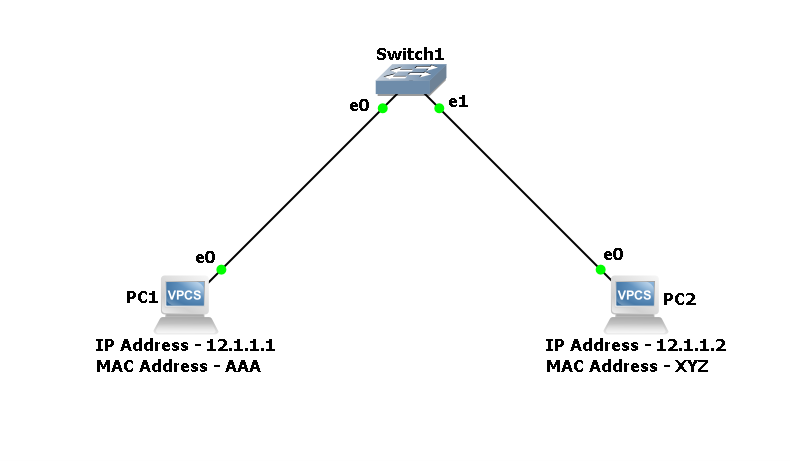
Understanding BGP Route Reflectors: Simplifying iBGP Full Mesh A detailed guide to BGP Route Reflectors—learn how they simplify iBGP full mesh, key reflection rules, configuration steps, loop prevention with Originator-ID and Cluster-ID, plus advantages and best practices for scalable and resilient network design. The Border Gateway Protocol (BGP) is the backbone of the internet, responsible … Read more