At the heart of IPsec and IKE lies a powerful concept — the Security Association (SA).
In today’s digital world, secure communication over public networks like the internet is critical. Whether it’s a remote employee accessing a company VPN or two data centers syncing sensitive information, IPsec is often the technology behind the scenes providing confidentiality, integrity, and authentication.
This blog explores:
- What is a Security Association?
- Why SAs are unidirectional
- SAs in IKE Phase 1 vs Phase 2
What is a Security Association (SA)?
A Security Association (SA) is like a contract between two parties that defines how they will protect the data they exchange. It’s a set of rules and parameters that determine the security mechanisms applied to a communication session.
Each SA includes:
- The encryption algorithm (e.g., AES, 3DES)
- The authentication method (e.g., HMAC-SHA256)
- A shared key or derived key
- A lifetime (how long the SA is valid)
- The protocol used (AH or ESP)
- A Security Parameter Index (SPI) — a unique identifier
- The mode of operation (tunnel mode or transport mode)
You can think of an SA as the blueprint for how two systems will talk securely — it says:
“We will encrypt using AES, authenticate with HMAC-SHA256, use this key, and maintain this security for 60 minutes.”
Why Security Associations Are Unidirectional
One of the most important characteristics of an SA is that it is unidirectional. This means that the SA used to protect traffic from Host A to Host B is not the same as the one used from Host B to Host A.
Here’s why:
- Different keys are often used for each direction.
- It allows independent control of encryption and authentication for each flow.
- It supports asymmetric policies — one direction might require stronger encryption than the other.
- It improves security granularity and allows individual rekeying.
Result:
- To establish a full duplex (two-way) secure communication, two SAs are always required — one for each direction.
Example:
- SA1: Protects data from Client → Server
- SA2: Protects data from Server → Client
This structure allows better management and security control over the encrypted channel.
Security Association in IKE: Phase 1 vs Phase 2
In IPsec using IKE (Internet Key Exchange), SAs are created during both Phase 1 and Phase 2. But they serve very different purposes.
🔹 Phase 1: IKE SA
Goal: Establish a secure, authenticated channel to negotiate future SAs.
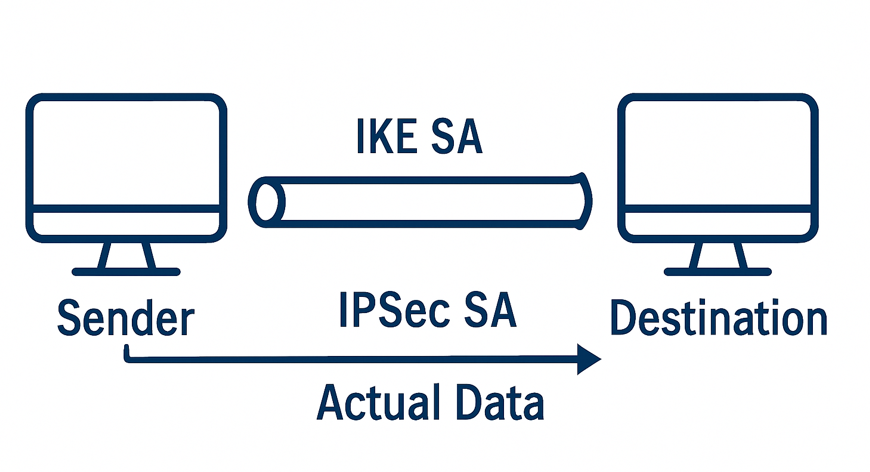
Phase 1 is where the IKE SA is established. This SA is not used to protect user data, but instead to secure future key negotiations and control messages between the peers.
It is established using either:
- Main Mode (6 messages)
- Aggressive Mode (3 messages)
What the IKE SA includes:
- Encryption and authentication algorithms for IKE messages
- Diffie-Hellman key exchange result
- Authentication credentials (certificates, PSK, etc.)
- Lifetime of the IKE SA
- Secure channel for further negotiation (Phase 2)
Once this IKE SA is established, it creates a secure tunnel that is used to exchange sensitive information, such as keys and IPsec policies.
🔸 Phase 2: IPsec SA
Goal: Define how actual IP traffic will be protected.
Once the secure IKE SA is in place, Phase 2 begins. This is where the IPsec SAs are negotiated — the ones that actually protect real-world traffic like emails, files, voice calls, etc.
Phase 2 uses Quick Mode (3 messages) and results in:
- Two unidirectional IPsec SAs (one in each direction)
- Selection of the IPsec protocol (AH or ESP)
- Traffic selectors (which IP addresses/subnets to protect)
- New encryption and authentication keys
- SA lifetime and rekeying settings
These SAs are what encrypt and authenticate the actual data packets sent between the two systems.
If the sender and receiver are already authenticated in IKE SA (Phase 1), why can’t we just start sending encrypted data directly? Why do we need IPsec SA (Phase 2)
Key Reasons We Still Need IPsec SA (Quick Mode / Phase 2)
1. Different Traffic, Different Protection
- IKE SA is used to protect IKE negotiations only.
- IPsec SA is used to selectively protect specific traffic (e.g., 10.0.0.0/24 to 172.16.0.0/24).
- You may want to protect only part of the traffic, not everything.
2. Key Separation = Better Security
- Reusing IKE SA keys for data traffic would be bad practice.
- IPsec SA uses new keys derived from IKE SA, to reduce attack surface.
- If IPsec keys are compromised, your control channel (IKE SA) is still safe.
3. Scalability and Flexibility
- One IKE SA can negotiate multiple IPsec SAs (e.g., multiple tunnels).
- You can:
- Rekey IPsec SAs without redoing IKE SA
- Establish different tunnels for different purposes (QoS, routing, etc.)
4. Lifetime Control
- IPsec SAs typically have shorter lifetimes than IKE SAs.
- You can control how often to rekey, expire, or renegotiate the data channels independently of the IKE channel.
5. Traffic Selectors & SPIs
- IPsec SA negotiation includes Traffic Selectors:
- Define what IPs, ports, and protocols to encrypt
- It also sets SPIs (Security Parameter Indexes):
- These are unique identifiers in each ESP/AH packet to match the right SA
Comparison between IKE SA and IPSec SA
| Feature | IKE SA (Phase 1) | IPsec SA (Phase 2) |
| Purpose | Secure IKE negotiation messages | Secure actual IP data traffic |
| Protocol | IKEv1 / IKEv2 | IPsec (ESP or AH) |
| Messages | 6 (Main Mode) or 3 (Aggressive Mode) | 3 (Quick Mode) |
| Direction | Typically bidirectional | Always unidirectional (2 SAs created) |
| Lifetime | Longer (e.g., 1 hour or more) | Shorter (e.g., 30 minutes or data limit) |
| Content | Auth method, DH key, IKE policy | Encryption/authentication method, SPI, traffic selectors |
| Usage | For negotiating IPsec SAs | For encrypting and decrypting IP packets |
Real-World Analogy
Imagine two people want to send secret letters to each other.
- Phase 1: They first agree on a safe way to communicate, like using a locked mailbox. This agreement (how to lock, key, mailbox location) is the IKE SA.
- Phase 2: They start writing and sending actual letters (the data), each using a specific envelope style, lock, and address — this is the IPsec SA.
Final Thoughts
Understanding Security Associations is critical when working with IPsec and IKE. They are the core of how encryption and authentication policies are enforced, how keys are managed, and how data is protected during transmission.
Here’s a quick recap:
- An SA is a set of rules for securing communication.
- All SAs are unidirectional — two are needed for two-way traffic.
- IKE SA (Phase 1) secures the key exchange.
- IPsec SA (Phase 2) secures actual data traffic.
Whether you’re a network engineer, security analyst, or just learning about VPNs, grasping the concept of Security Associations will help you better understand how secure networking truly works.

