Auto Discovery Virtual Private Network
ADVPN is an IKE and IPsec-based solution that enables direct connectivity between all sites by creating on-demand tunnels between spokes. It offers the benefits of a full-mesh topology while ensuring scalability with minimal configuration. With ADVPN, spoke-to-spoke traffic no longer has to pass through the hub.
In this blog, we’ll guide you step by step to configure ADVPN on FortiGate firewalls within the GNS3 simulator. By the end, you’ll not only understand the process but also gain hands-on experience in setting up a dynamic, automated VPN.
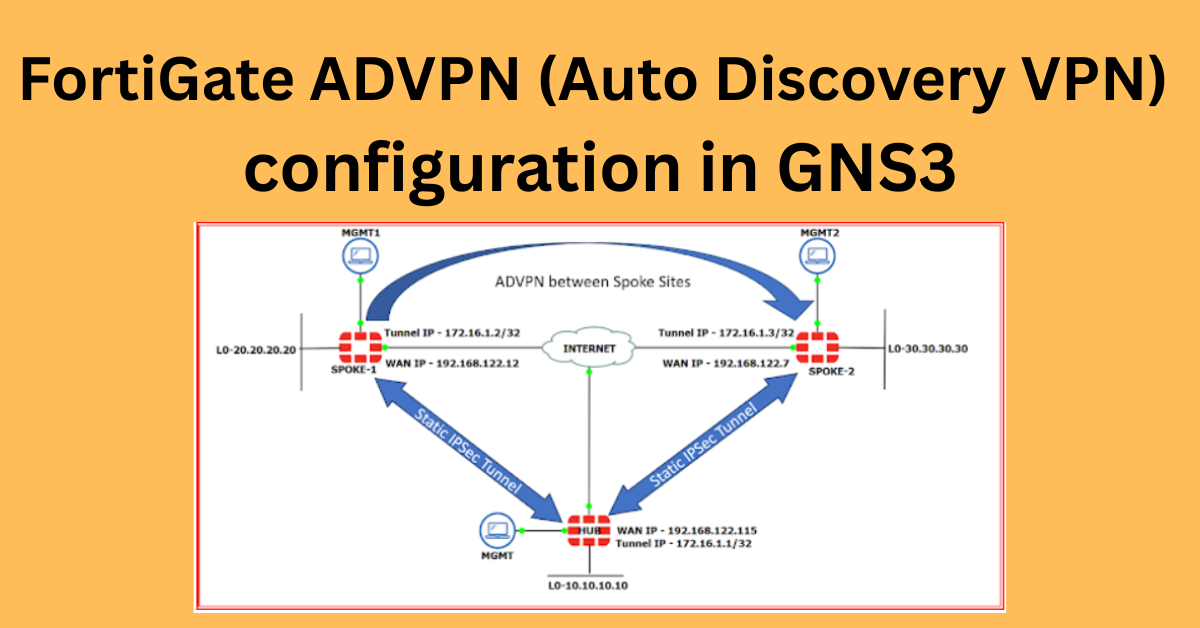
I am using the following topology to explore and understand the concept and configuration. Refer to the diagram and accompanying details below to get familiar with the setup.

To set up the environment, I configured Port1 on all three FortiGate devices (1 Hub and 2 Spokes) as the DHCP-enabled interface connected to the internet via NAT0. For management purposes, I utilized Port2 with DHCP enabled to simplify connectivity and control.
On the LAN side, I created a Loopback interface for each device and assigned a unique IP address for the internal network. The detailed IP schema is as follows:
Hub Configuration:
- WAN IP Address: 192.168.122.115
- Tunnel IP: 172.16.1.1
- LAN (Loopback0): 10.10.10.10
Spoke-1 Configuration:
- WAN IP Address: 192.168.122.12
- Tunnel IP: 172.16.1.2
- LAN (Loopback0): 20.20.20.20
Spoke-2 Configuration:
- WAN IP Address: 192.168.122.7
- Tunnel IP: 172.16.1.3
- LAN (Loopback0): 30.30.30.30
Let’s dive into the configuration! To make it easier to follow, I’ve broken the configuration steps into four key parts:
- VPN Configuration
- IP Address Configuration on the VPN Tunnel Interface
- Policy Configuration
- BGP Configuration
Step by Step Process – Let’s verify the WAN connectivity between SPOKE-1 and the HUB, as well as between SPOKE-1 and SPOKE-2, in both directions.

Great! With WAN reachability confirmed, let’s begin the VPN configuration. We’ll start at the HUB end, as it serves as the central device in this topology. Next, the SPOKE devices will establish the VPN connection with the HUB site.
1.1 Navigate to the VPN section and click on IPSec VPN. Currently, there are no existing policies. To create a new VPN, click on Create New and select the IPSec Tunnel.

1.2 Select Template Type as Custom, give your VPN a name, and click Next. Alternatively, you can also create the VPN using the Hub-and-Spoke Template.

1.3 In the Network section, configure the settings as shown in the screenshot below. Keep the following points in mind:
- Set Remote Gateway to Dialup User.
- Choose the WAN interface for the Interface.
- In the Advanced section, ensure that Auto Discovery Sender is enabled.

1.4 In the Authentication section, assign a password and make sure to note it, as the same password will be used for the Spoke sites. Select IKE Version 2 and configure the Phase 1 IPSec Proposal and Phase 2 Parameters as shown in the screenshot below. Ensure that all parameters match the Spoke site configuration, so be sure to remember them.
Click the OK button once all selections are made according to the requirements.


With the first configuration part complete, let’s move on to the second part: configuring the IP address on the tunnel interface.
2. After creating the VPN, the tunnel interface is automatically generated under Physical Port1, but it will have a default IP address.

Double-click on the tunnel interface and assign the IP address based on the IP address schema mentioned earlier. and click on OK button.
Enable PING under Administrative Access and click the OK button.

3. Now it’s time to create the firewall policies. We’ll set up three policies for this configuration:
3.1 Tunnel (Overlay) to LAN (Loopback interface)3.2 LAN to Tunnel (Overlay)3.2 Spoke-to-Spoke Policy (Overlay Tunnel to Overlay Tunnel)

Overlay (Spoke) Tunnel to Lan Policy –

LAN To Overlay(Spoke) Tunnel Policy –

Spoke To Spoke Policy –

4. With the policy configuration complete, the next step is to establish the BGP session with the Spokes.
On the Hub side, we’ll create a BGP neighborship group to simplify the setup. By adding the BGP neighbor IPs and their corresponding remote AS numbers to this group, we avoid the need to configure each Spoke individually.
The BGP sessions will be established using the tunnel IPs, which will become reachable once the Spoke configuration is complete.
Steps:
- Navigate to the Network section in the left pane and click on BGP. Assign the Local AS Number as
65511and set a Router ID (I’ve configured it as1.1.1.1). - Next, click on Neighbor Group, create a group, and assign the Neighbor AS Number. Since we’re setting up iBGP, the local and remote AS numbers will be the same.

4.3 Next, click on Neighbor Ranges and select Create New. In the new window, add the BGP neighbor IP range. In this setup, we are establishing BGP neighborship using the tunnel IPs.

After that Double click on Neighbor ranges group which ic created now and enable the route reflector and other parameters as per below snap –

4.4 In the Networks tab, add the prefixes to be advertised through the BGP protocol. Here, we will advertise the LAN (Loopback) network. Once done, click the Apply button to save the configuration.

The configuration on the Hub side is now complete.
==============================================================
Spoke-1 Configuration –
We will now proceed to complete the Spoke configuration by following the same steps as outlined earlier.
let’s verify WAN reachability using the WAN IPs. The ping test confirms successful connectivity!

1. VPN Configuration –

Ensure the IP address is set to the WAN IP of the Hub site. Additionally, don’t forget to enable Auto-Discovery Receiver and Device Creation.

Phase-1 Proposal-

Phase2 Parameters – Remember to enable the Auto Negotiate option. Once all the settings are configured as shown in the snapshot below, click the OK button to apply them.

2. The tunnel interface is automatically created after configuring the VPN.

Double-click on it to assign the IP address.

3. Let’s configure the policy for LAN to Hub (Overlay) and Hub to LAN traffic.
LAN to HUB(Overlay) –

Overlay to LAN Policy –

After creating the policy, the VPN tunnel status shows as UP.

4. Lets configure the BGP now –

Advertise the local network in BGP and click the Apply button to save the changes.

Wow, that’s great! The Spoke-1 configuration is now complete.
Next, let’s verify the reachability between the Spoke-1 tunnel and the Hub tunnel, as well as the BGP status.
HUB to SPOKE-1 reachability and BGP status –

SPOKE-1 to HUB Reachability and BGP status –

==============================================================
Now, let’s configure SPOKE-2 following the same steps as SPOKE-1. The only difference will be the change in the IP address.
Here are some snapshots from the SPOKE-2 configuration:
1. VPN Configuration –



2. IP address configuration on Tunnel Interface –

3. Policy Configuration –


As you can see, the tunnel is now showing as UP.

That’s great! You’re now able to reach the HUB tunnel IP from SPOKE-2.

4. Lets configure the BGP –


That’s excellent! The BGP neighborship has successfully come up as well.

Now that the SPOKE-2 configuration is complete, let’s verify if SPOKE-1 is reachable from SPOKE-2.

Exactly! The dynamic tunnel between SPOKE-1 and SPOKE-2 is established, and now both LAN networks are reachable from each other. Great job!
Let’s check the status from the SPOKE-1 site to confirm the tunnel and connectivity.

That’s fantastic! From the SPOKE-1 site, you can successfully ping the SPOKE-2 LAN, confirming that the setup is working as expected.


At the HUB end, the VPN section shows that two dial-up VPNs are UP, indicating that both SPOKE-1 and SPOKE-2 are successfully connected.

In conclusion, we have successfully configured and verified the connectivity between SPOKE-1, SPOKE-2, and the HUB using dynamic VPN tunnels. The BGP neighborships are stable, and both LAN networks are reachable, demonstrating the effectiveness of the configuration.
Thank You !!!