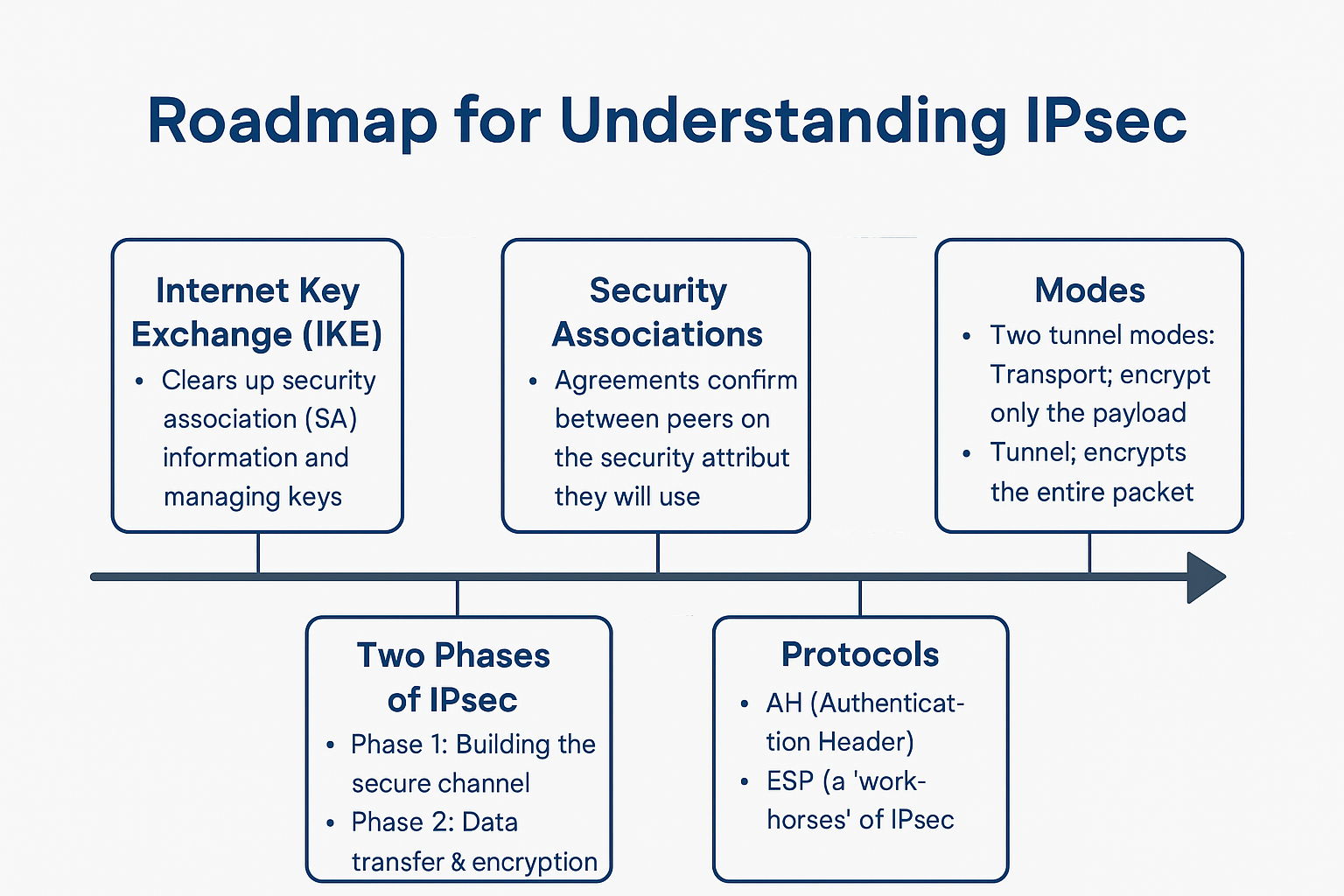
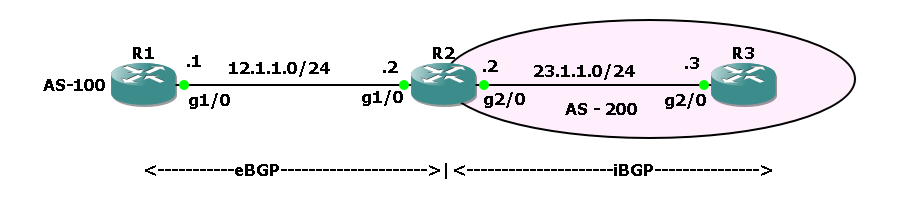
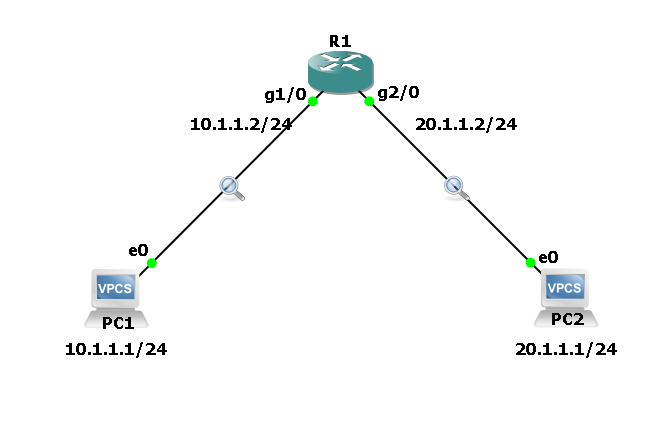
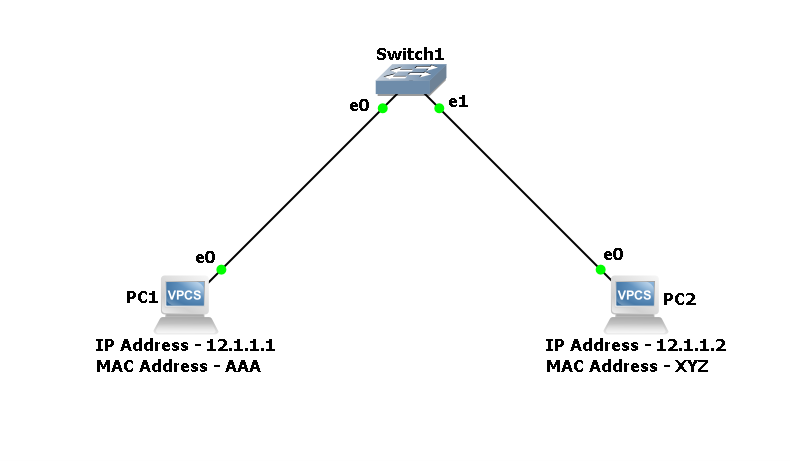
BGP Messages Explained: A Beginner-Friendly Guide
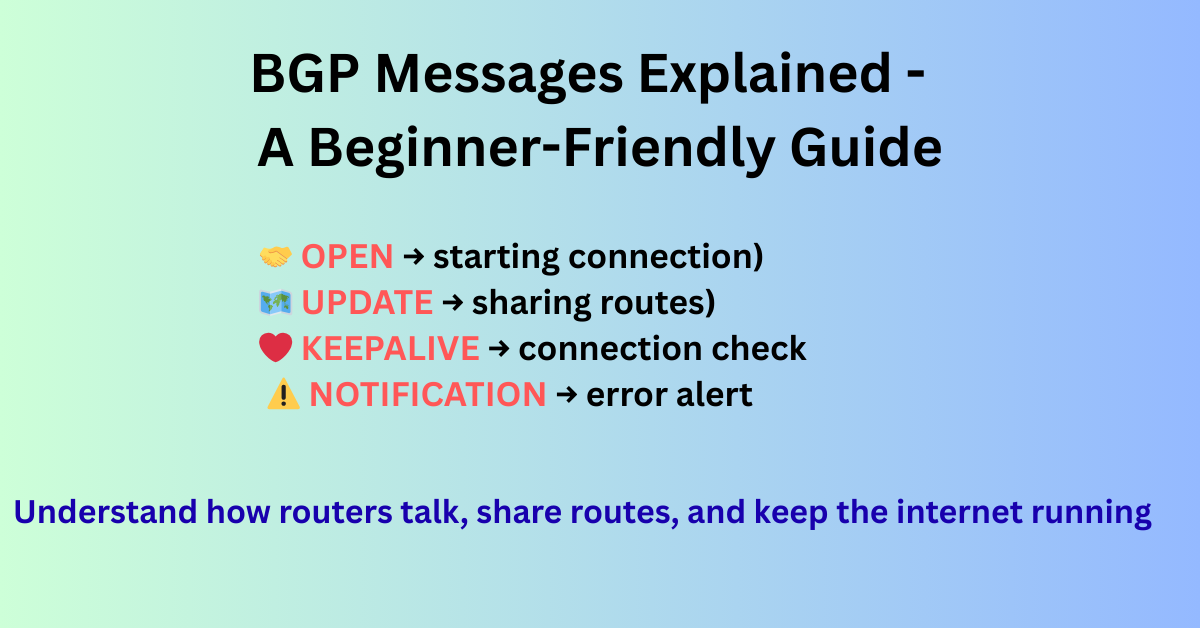
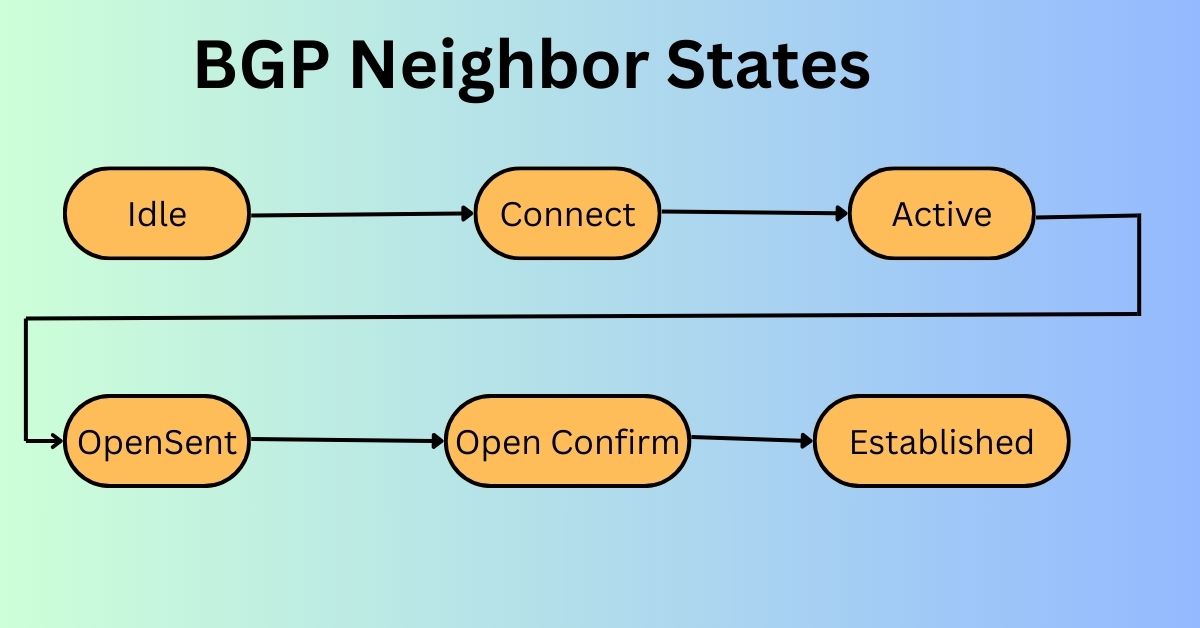
BGP Messages Explained: A Beginner-Friendly Guide If you’ve ever wondered “How does the internet know where to send my data?”, the answer is a protocol called BGP (Border Gateway Protocol). Think of BGP as the GPS system of the internet. It helps your data find the best and most reliable path to its destination. But … Read more