In today’s world, where secure communication is essential — whether you’re connecting to a VPN at work or linking two sites over the internet — a behind-the-scenes hero makes it all possible: IKE, or Internet Key Exchange.
This blog will break down what IKE is, how it evolved, how it works, and the technical details behind both IKEv1 and IKEv2, in a way that’s easy to understand — even if you’re not a security expert.
Why Do We Need IKE?
In a world where sensitive data travels across public and untrusted networks like the internet, we face three key challenges:
- How do we ensure the data hasn’t been altered? (Integrity)
- How do we know who we’re talking to? (Authentication)
- How do we prevent others from seeing our data? (Confidentiality)
To solve this, we use encryption — but encryption needs keys, and for security, these keys must be:
- Exchanged securely,
- Generated dynamically,
- And known only to the two trusted parties.
Here’s the problem:
How can two devices securely agree on encryption keys, over a network that anyone can listen to?
That’s exactly what IKE solves.
IKE is like a private meeting between two parties, where they:
- Agree on how to talk securely,
- Prove who they are,
- And secretly pass the keys to each other without anyone else being able to intercept or understand them.
So, without IKE, we wouldn’t be able to set up secure VPN tunnels, encrypted site-to-site links, or even basic IP-level encryption. It’s the foundation of automated, secure communication between devices and networks.
What Is IKE (Internet Key Exchange)?
Internet Key Exchange (IKE) is a security protocol used to:
- Establish a secure and trusted channel between two systems,
- Exchange cryptographic keys over an untrusted network,
- And create what’s called a Security Association (SA) — a shared agreement about how to encrypt and authenticate future traffic.
In simple terms:
IKE is a conversation that two devices have before they start sending private data — a conversation about how to stay safe, how to prove who they are, and how to share a secret that no one else can know.
Think of IKE like this:
- Two strangers (computers) meet in a coffee shop (the internet).
- They want to talk in a private language (encryption).
- But they have to:
- Agree on which language to use (encryption methods),
- Prove they are who they say they are (authentication),
- And secretly share a password (key exchange) without anyone else overhearing.
- IKE makes all that possible — automatically, securely, and quickly.
Evolution of IKE
IKE has gone through two major versions:
🔹 IKEv1 (First version)
- Introduced in the late 1990s.
- Defined in RFC 2409.
- Works in two phases:
- Phase 1: Creates a secure channel.
- Phase 2: Sets up secure data tunnels.
- Has two modes in Phase 1: Main Mode and Aggressive Mode.
🔹 IKEv2 (Current version)
- Defined in RFC 7296.
- Much simpler, faster, and more secure.
- Supports NAT traversal, mobility, and better error handling.
- Uses fewer messages and does not require different modes.
Today, IKEv2 is the recommended standard for VPNs and secure tunnels.
How Does IKE Work?
IKE works in two main phases:
Phase 1: Build a Secure Channel
- Devices agree on which algorithms to use (encryption, hashing, etc.).
- They exchange Diffie-Hellman keys to create a shared secret.
- They authenticate each other using a password (PSK), certificate, or other methods.
- The result is a secure IKE SA (Security Association) — a protected path for future communication.
Phase 2: Negotiate Data Protection
- Devices use the secure channel to create one or more Child SAs.
- These SAs define how to encrypt and authenticate the actual data.
IKEv1 Phases Overview
| Phase | Purpose | Messages |
| Phase 1 | Establish a secure, authenticated channel (IKE SA) | Main Mode (6 messages) or Aggressive Mode (3 messages) |
| Phase 2 | Negotiate IPsec SAs to protect user data (Child SA) | Quick Mode (typically 3 messages) |
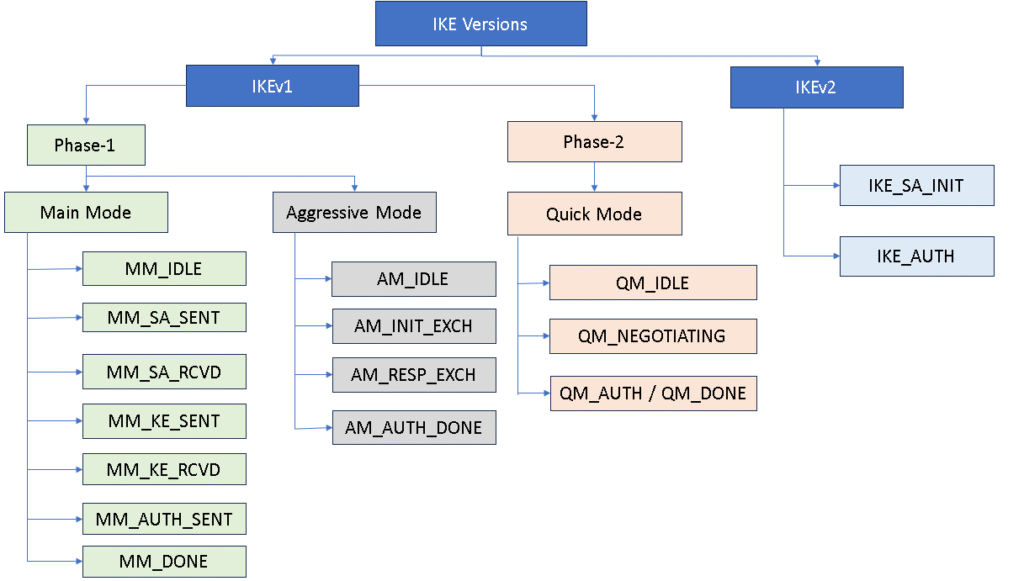
The diagram below captures all IKE versions along with their phases and modes, providing a complete view that makes the overall concept easier to understand.
Key Components of IKE
| Component | Purpose |
| Security Association (SA) | A contract between two devices about how to protect data. |
| Diffie-Hellman (DH) | A method to securely generate shared keys. |
| Nonce | A random value used to ensure security and prevent replay attacks. |
| Authentication | Verifies identities using passwords, certificates, or EAP. |
| Encryption Algorithms | Tools like AES used to scramble data. |
| Integrity Algorithms | Tools like SHA used to ensure data hasn’t been changed. |
IKEv1 – In Detail
In IKEv1, Phase 1 can be done in two ways:
- Main Mode (secure but slower)
- Aggressive Mode (faster but less secure)
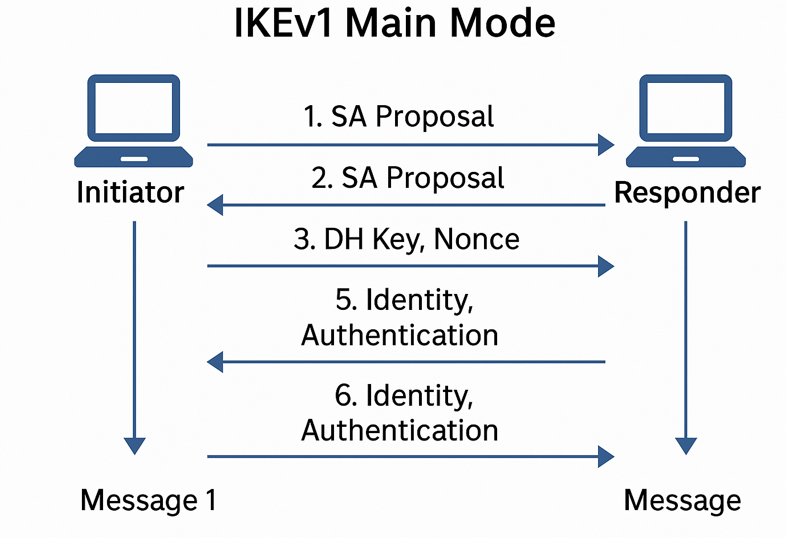
Let’s focus on Main Mode, which uses 6 messages to build a secure connection.
Phase1 Main Mode – 6 Messages with State Transitions
This phase establishes a secure channel (IKE SA) between the peers using encryption and authentication.
| Message | Direction | State Transition | Contents | What Happens |
| 1 | Initiator → Responder | MM_IDLE → MM_SA_SENT | SA Proposal | Initiator proposes IKE parameters (encryption, hashing, DH group, etc.) |
| 2 | Responder → Initiator | MM_SA_SENT → MM_SA_RCVD | SA Response | Responder selects matching SA proposal |
| 3 | Initiator → Responder | MM_SA_RCVD → MM_KE_SENT | KE (DH public value), Nonce | Initiator sends Diffie-Hellman key and nonce |
| 4 | Responder → Initiator | MM_KE_SENT → MM_KE_RCVD | KE (DH public value), Nonce | Responder sends its own DH key and nonce |
| 5 | Initiator → Responder | MM_KE_RCVD → MM_AUTH_SENT | IDi (Initiator ID), Authentication (encrypted) | Initiator sends identity and authentication info (encrypted) |
| 6 | Responder → Initiator | MM_AUTH_SENT → MM_DONE | IDr (Responder ID), Authentication (encrypted) | Responder sends identity and authentication info (encrypted) |
Step-by-Step: What Happens in Main Mode –
- Messages 1–2: Agree on which encryption and hashing algorithms to use.
- Messages 3–4: Exchange Diffie-Hellman values and nonces to create a shared secret.
- Messages 5–6: Exchange and verify identities (usernames/certs) and authentication.
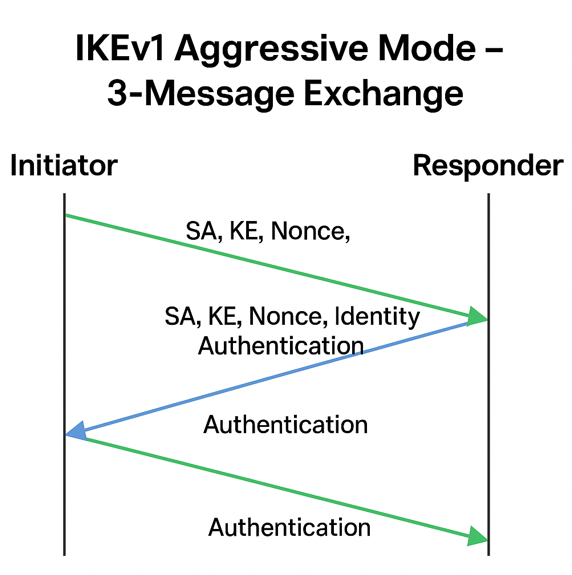
Phase1 Aggressive Mode – 3 Messages with State Transitions
Aggressive Mode is used in Phase 1 (alternative to Main Mode). It completes the negotiation in 3 messages and is faster but less secure because identities are not encrypted.
| Message | Direction | State Transition | Contents | What Happens |
| 1 | Initiator → Responder | AM_IDLE → AM_INIT_SENT | SA Proposal, KEi, Ni, IDi | Initiator sends IKE proposal, Diffie-Hellman key, nonce, and its identity (IDi) in clear text |
| 2 | Responder → Initiator | AM_INIT_SENT → AM_RESP_RCVD | SA Response, KEr, Nr, IDr, Authentication | Responder selects proposal, sends DH key, nonce, its ID, and authentication (can be cert, PSK, etc.) |
| 3 | Initiator → Responder | AM_RESP_RCVD → AM_DONE | Authentication | Initiator sends authentication to confirm the exchange |
Phase 2 (Quick Mode)
- Negotiates the actual IPsec tunnel (encryption of real data).
- Usually involves 3 messages.
- Uses the secure channel from Phase 1.
Phase2 Quick Mode – 3 Messages with State Transitions
Quick Mode is always used in Phase 2 and negotiates IPsec SAs (used to secure actual data traffic). It runs over the secure channel built during Phase 1 (either via Main or Aggressive Mode).
| Message | Direction | State Transition | Contents | What Happens |
| 1 | Initiator → Responder | QM_IDLE → QM_INIT_SENT | IPsec SA Proposal, Nonce, optional ID, optional KE | Initiator proposes IPsec encryption/authentication parameters and sends a nonce |
| 2 | Responder → Initiator | QM_INIT_SENT → QM_RESP_RCVD | IPsec SA Response, Nonce, optional ID, optional KE | Responder selects acceptable proposal and returns its own nonce and IDs |
| 3 | Initiator → Responder | QM_RESP_RCVD → QM_DONE | Authentication confirmation (optional hash or sig) | Final confirmation and optional authentication hash to finalize IPsec SA |
IKEv2 – In Detail
IKEv2 combines Phase 1 and Phase 2 of IKEv1 into a single streamlined exchange. It eliminates Main/Aggressive/Quick modes and instead uses two clearly defined exchanges:
IKE_AUTH → Exchange identities, authenticate, and establish IPsec SA (like Phase 2)
IKE_SA_INIT → Establish secure IKE SA (like Phase 1)
🔹 IKEv2 Message Flow and State Transitions
| Exchange | Message | Direction | State Transition | Contents | What Happens |
| IKE_SA_INIT | 1 | Initiator → Responder | IKEV2_INIT_START → IKEV2_INIT_SENT | SA Proposal, KEi (DH value), Ni (Nonce), SPIi | Initiator sends IKE SA parameters and starts DH key exchange |
| 2 | Responder → Initiator | IKEV2_INIT_SENT → IKEV2_INIT_DONE | SA Response, KEr, Nr, SPIr | Responder replies with chosen SA, DH key, and its nonce | |
| IKE_AUTH | 3 | Initiator → Responder | IKEV2_INIT_DONE → IKEV2_AUTH_SENT | IDi, AUTH (initiator), Child SA Proposal, Traffic Selectors, Encrypted | Initiator authenticates, provides identity, and proposes IPsec (Child SA) |
| 4 | Responder → Initiator | IKEV2_AUTH_SENT → IKEV2_DONE | IDr, AUTH (responder), Child SA Response, Traffic Selectors, Encrypted | Responder authenticates and completes Child SA (IPsec SA) negotiation |
Step-by-Step: What Happens in Each Exchange
1. IKE_SA_INIT
- Each side proposes encryption and hashing options.
- They exchange Diffie-Hellman values.
- They exchange nonces for randomness.
- Result: They derive a shared secret key.
2. IKE_AUTH
- Each side sends their identity (certificate, PSK, or EAP method).
- Authentication is performed.
- First Child SA (data encryption rules) is established.
After this step, the devices can securely send encrypted traffic.
Summary
- IKE is the brain behind secure VPN connections.
- It builds trust, negotiates security settings, and protects data in transit.
- IKEv1 works but is older and more complex.
- IKEv2 is the modern, simplified, and more secure version.

